Text
Page: 1
Do you trust
that
certificate?
Page: 6
ntroduction
to
modern
cryptograph
Page: 7
www.hyuki.com/cr/
Page: 8
Transport
Layer
Security
Page: 9
Secure
Socket
Layer
Page: 12
A web
application
Page: 13
Receives
requests
Page: 14
Calls
external
resources
Page: 15
That
handles
secret
information
Page: 16
How does
app trust
them?
Page: 18
Public-key
nfrastructur
Page: 19
Server
certificate
Page: 20
Signed by
Certificate
Authority
Page: 21
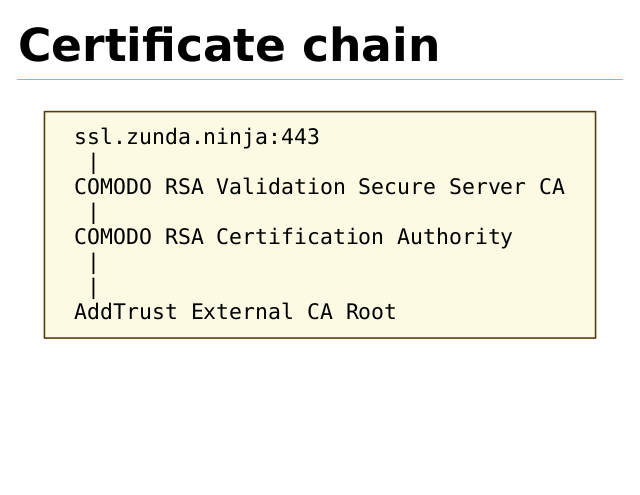
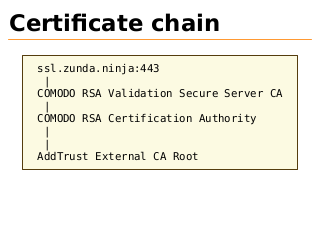
Certificate chain
ssl.zunda.ninja:443
|
COMODO RSA Validation Secure Server CA
|
COMODO RSA Certification Authority
|
|
AddTrust External CA Root
Page: 24
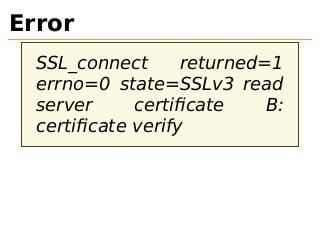
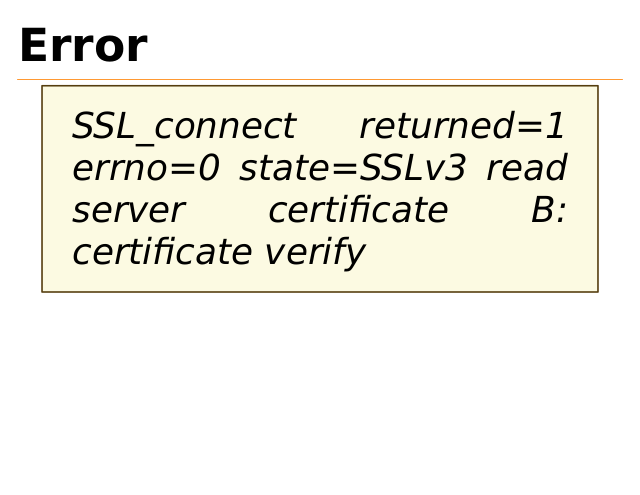
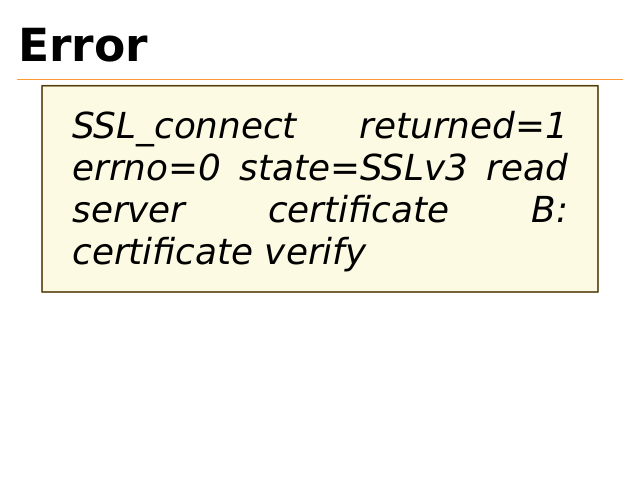
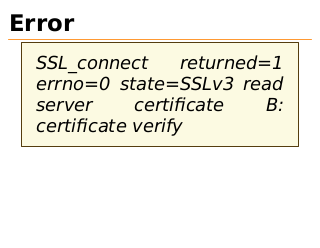
Error
SSL_connect
returned=1
errno=0 state=SSLv3 read
server
certificate
B:
certificate verify
Page: 25
I did not
change
anything!
Page: 27
Something
outside
has
changed
Page: 28
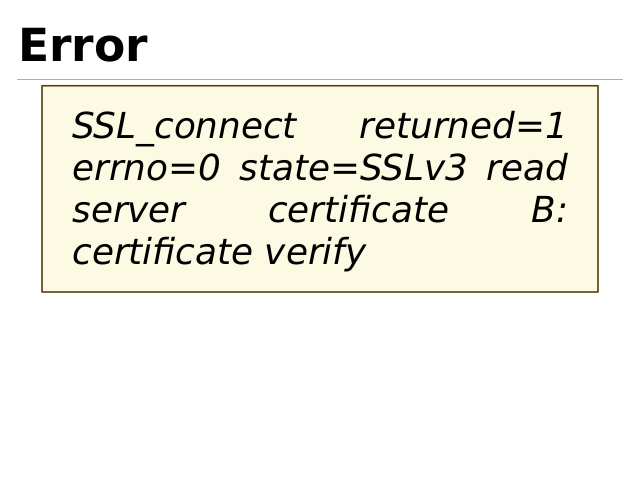
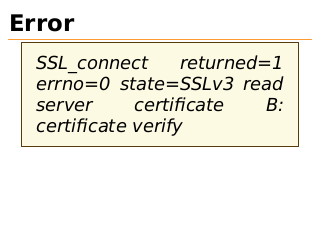
Error
SSL_connect
returned=1
errno=0 state=SSLv3 read
server
certificate
B:
certificate verify
Page: 29
Certificate chain
ssl.zunda.ninja:443
|
[NEW] Some Server CA
|
[NEW] Some Certification Authority
|
|
[NEW] Unknown CA Root
Page: 30
2014-09
1024 bit
hash
Page: 32
Replace
with new
certs
Page: 34
That app
does not
know
Page: 35
Certificate chain
ssl.zunda.ninja:443
|
[NEW] Some Server CA
|
[NEW] Some Certification Authority
|
|
[????]
Page: 36
Error
SSL_connect
returned=1
errno=0 state=SSLv3 read
server
certificate
B:
certificate verify
Page: 40
Include
new CA
cert in app
Page: 41
Monkey
patch to
use it
Page: 42
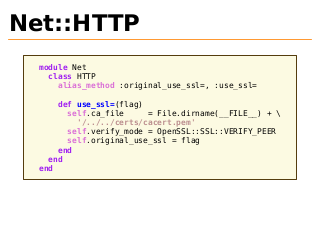
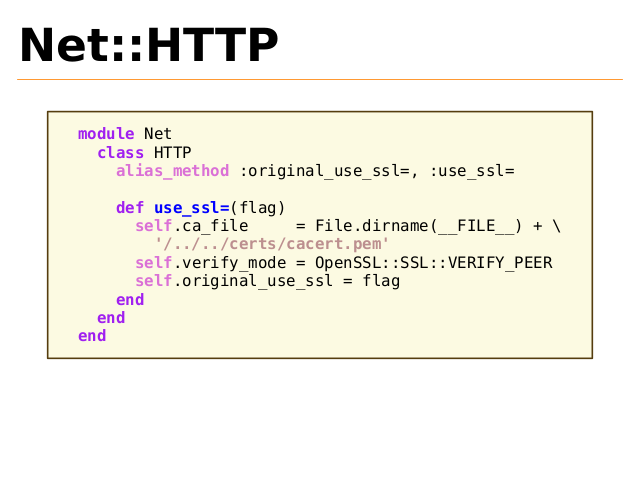
Net::HTTP
module Net
class HTTP
alias_method :original_use_ssl=, :use_ssl=
def use_ssl=(flag)
self.ca_file
= File.dirname(__FILE__) + \
'/../../certs/cacert.pem'
self.verify_mode = OpenSSL::SSL::VERIFY_PEER
self.original_use_ssl = flag
end
end
end
Page: 43
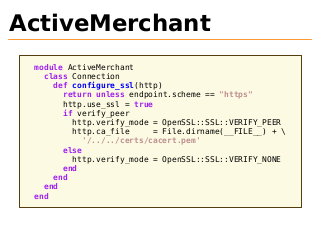
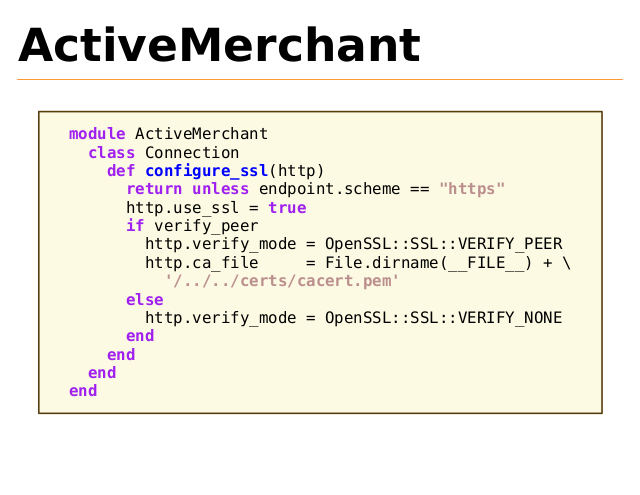
ActiveMerchant
module ActiveMerchant
class Connection
def configure_ssl(http)
return unless endpoint.scheme == "https"
http.use_ssl = true
if verify_peer
http.verify_mode = OpenSSL::SSL::VERIFY_PEER
http.ca_file
= File.dirname(__FILE__) + \
'/../../certs/cacert.pem'
else
http.verify_mode = OpenSSL::SSL::VERIFY_NONE
end
end
end
end
Page: 44
System's
CA certs
Page: 46
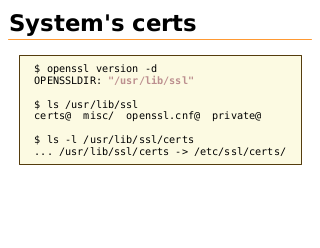
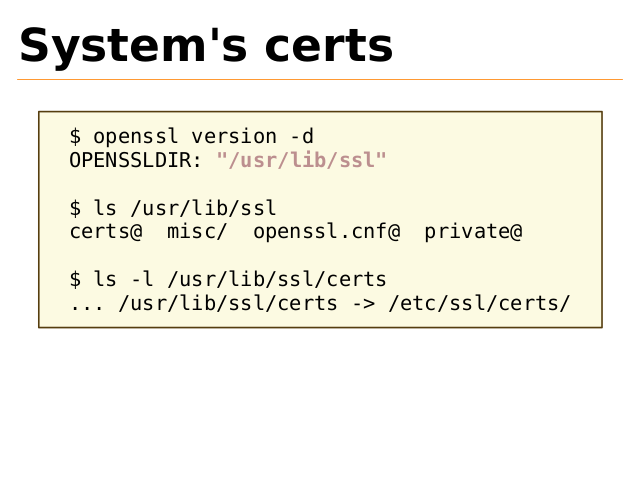
System's certs
$ openssl version -d
OPENSSLDIR: "/usr/lib/ssl"
$ ls /usr/lib/ssl
certs@ misc/ openssl.cnf@
private@
$ ls -l /usr/lib/ssl/certs
... /usr/lib/ssl/certs -> /etc/ssl/certs/
Page: 47
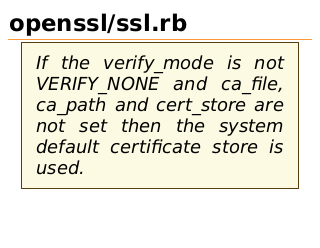
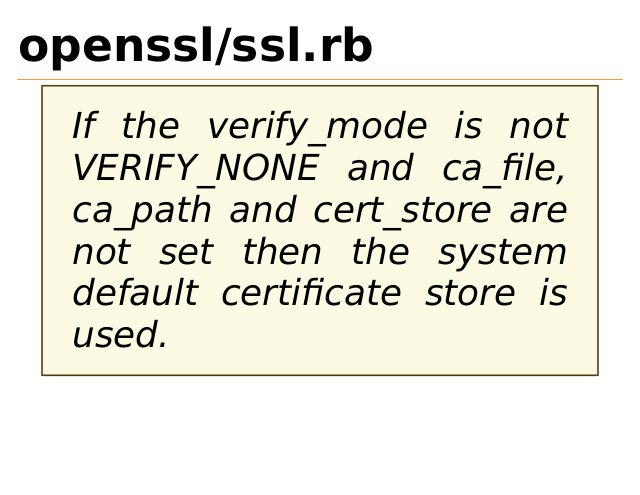
openssl/ssl.rb
If the verify_mode is not
VERIFY_NONE and ca_file,
ca_path and cert_store are
not set then the system
default certificate store is
used.
Page: 48
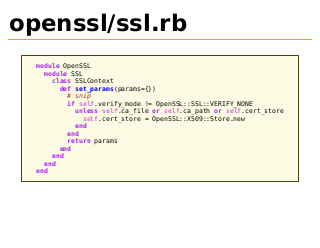
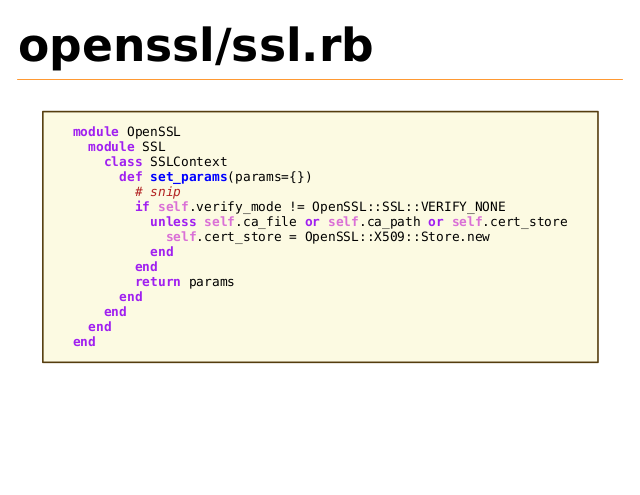
openssl/ssl.rb
module OpenSSL
module SSL
class SSLContext
def set_params(params={})
# snip
if self.verify_mode != OpenSSL::SSL::VERIFY_NONE
unless self.ca_file or self.ca_path or self.cert_store
self.cert_store = OpenSSL::X509::Store.new
end
end
return params
end
end
end
end
Page: 49
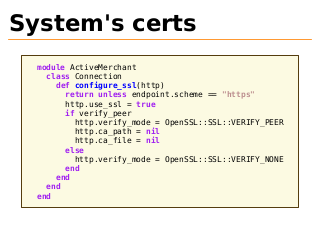
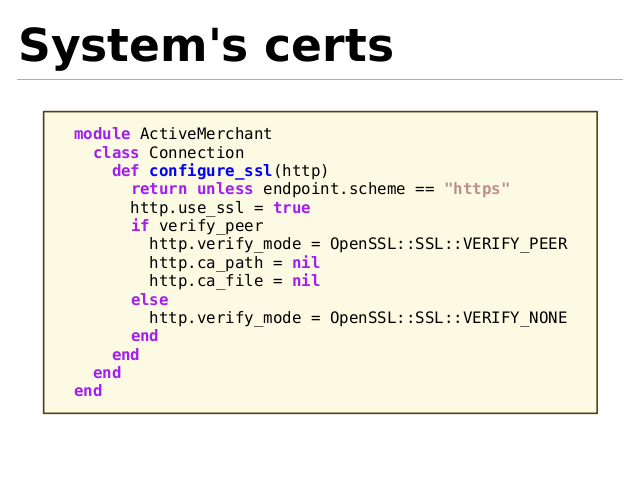
System's certs
module ActiveMerchant
class Connection
def configure_ssl(http)
return unless endpoint.scheme == "https"
http.use_ssl = true
if verify_peer
http.verify_mode = OpenSSL::SSL::VERIFY_PEER
http.ca_path = nil
http.ca_file = nil
else
http.verify_mode = OpenSSL::SSL::VERIFY_NONE
end
end
end
end
Page: 51
Remember
what we
trust
Page: 52
What are
coming?
Page: 54
Symantec
certs on
Google
products?
Page: 55
Will there
be
updates?
Page: 56
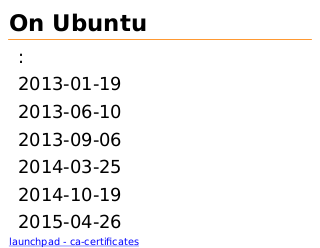
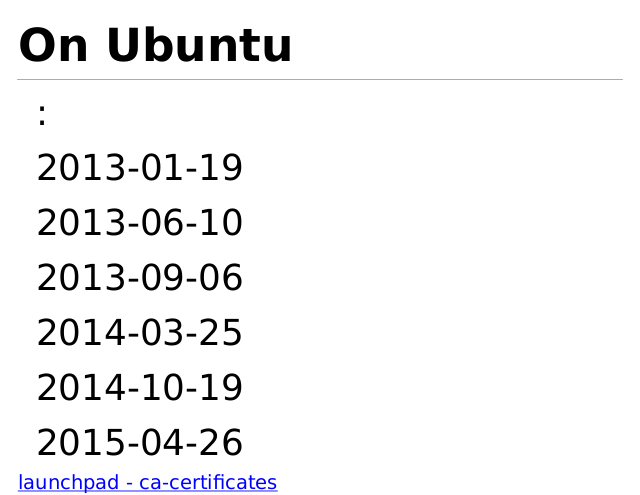
On Ubuntu
:
2013-01-19
2013-06-10
2013-09-06
2014-03-25
2014-10-19
2015-04-26
launchpad - ca-certificates
Page: 57
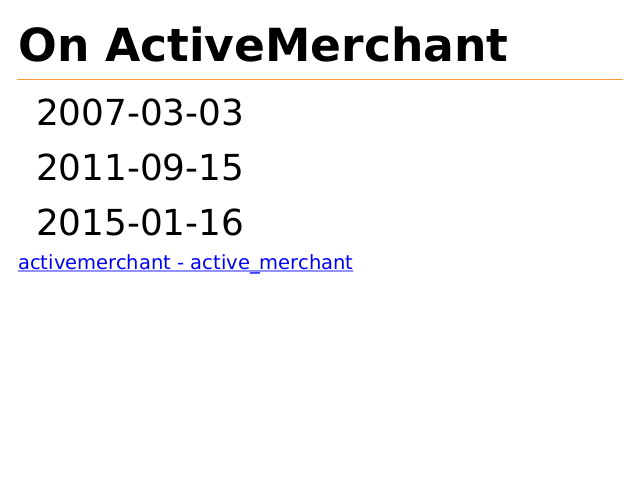
On ActiveMerchant
2007-03-03
2011-09-15
2015-01-16
activemerchant - active_merchant
Page: 58
Remember
and be
prepared!
Page: 60
www.hyuki.com/cr/
Page: 62
Certificate
Revocation
List
Page: 63
How are
we
updating
this?
Page: 64
SSL and
TLS1.0
will be
disabled
Page: 66
Payment
Card
Industry
Page: 67
Remember
what we
trust
Page: 68
URLs
暗号技術入門
Phasing out Certificates with
1024-bit RSA Keys
SHA-1
AWS to Switch to SHA256
Hash Algorithm for SSL
Certificates
Sustaining Digital Certificate
Page: 69
CC BY-ND 4.0
Presented as a lightning talk in
RubyKaigi 2015 on 2015-12-12
Copyright 2015 by zunda
<zundan@gmail.com>
























![Certificate chain
ssl.zunda.ninja:443
|
[NEW] Some Server CA
|
[NEW] Some Certification Authority
|
|
[NEW] Unknown CA Root](28.png)




![Certificate chain
ssl.zunda.ninja:443
|
[NEW] Some Server CA
|
[NEW] Some Certification Authority
|
|
[????]](34.png)















































![Certificate chain
ssl.zunda.ninja:443
|
[NEW] Some Server CA
|
[NEW] Some Certification Authority
|
|
[NEW] Unknown CA Root](mini-28.png)




![Certificate chain
ssl.zunda.ninja:443
|
[NEW] Some Server CA
|
[NEW] Some Certification Authority
|
|
[????]](mini-34.png)